El fortalecimiento de la ciberseguridad nacional se ha convertido en una prioridad estratégica para los Estados en la era digital. En este contexto, el Centro Nacional de Ciberseguridad (CNCS) de la República Dominicana ha logrado consolidarse como una institución líder en el Caribe y América Latina. Desde su creación, y particularmente durante el período 2020-2024, el CNCS ha implementado una política pública integral que articula la prevención, la respuesta a incidentes, la cooperación interinstitucional y la formación de capacidades técnicas y ciudadanas. Aquí observo algunos de los logros más relevantes del CNCS, su posicionamiento frente a sus pares regionales y plantea estrategias para fortalecer su papel como servicio de ciberseguridad más robusto y efectivo. Lo siguiente NO es de índole “clasificado”,
I. Consolidación del CNCS como autoridad nacional en ciberseguridad
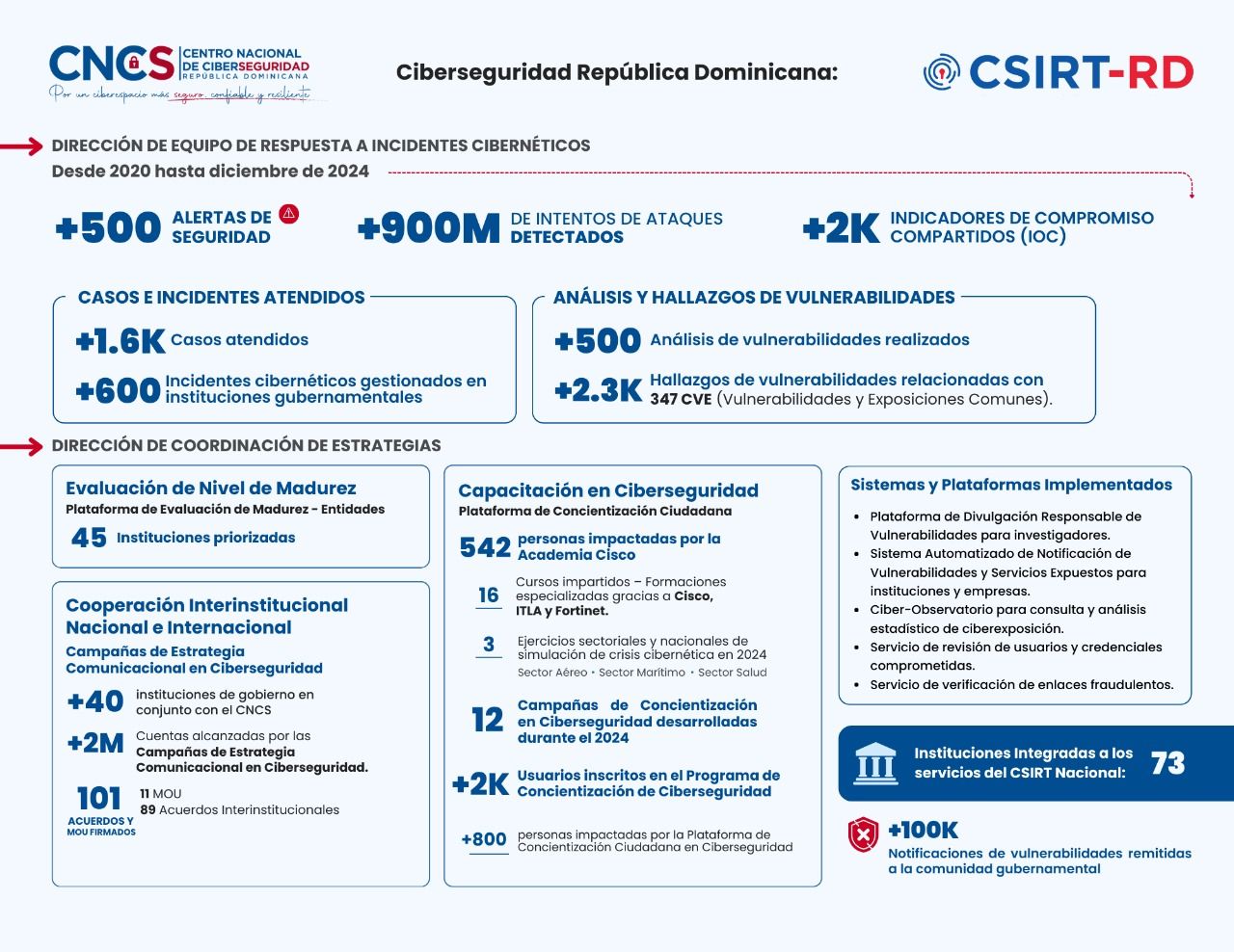
Desde 2020, el CNCS ha establecido una estructura dual: la Dirección de Respuesta a Incidentes Cibernéticos (CSIRT-RD) y la Dirección de Coordinación de Estrategias. El rendimiento (imagen aquí adjunto) es meritorio. Según las cifras PUBLICAS, . . . El CSIRT-RD ha gestionado más de 500 alertas de seguridad, detectado más de 900 millones de intentos de ataque y compartido más de 2,000 indicadores de compromiso (IOC) con instituciones nacionales e internacionales (CNCS, 2024). En cuanto a la gestión de incidentes, se han atendido más de 1,600 casos, de los cuales 600 corresponden a instituciones gubernamentales. Estas cifras, que reflejan un aumento sostenido en la capacidad de detección y respuesta, representan un avance considerable para un país en vías de consolidar su ecosistema digital.
En el ámbito del análisis técnico, el CNCS ha realizado más de 500 evaluaciones de vulnerabilidades, identificando 2,300 hallazgos asociados con 347 vulnerabilidades y exposiciones comunes (CVE) (CNCS, 2024). Este volumen de trabajo técnico es comparable con centros nacionales de ciberseguridad de economías intermedias, lo que muestra un nivel de madurez institucional notable en el Caribe. La combinación de detección temprana, análisis técnico y cooperación activa coloca al CNCS como un referente regional.
II. Desarrollo de capacidades institucionales y cooperación interinstitucional
El CNCS no solo ha enfocado su labor en la respuesta técnica, sino también en la madurez organizacional de las instituciones públicas. A través de su Plataforma de Evaluación de Nivel de Madurez, ha priorizado 45 instituciones, permitiendo medir el grado de preparación en materia de ciberseguridad y planificar intervenciones específicas (CNCS, 2024). En paralelo, la Dirección de Coordinación de Estrategias ha promovido la cooperación nacional e internacional con más de 40 instituciones gubernamentales, firmando 101 acuerdos y memorandos de entendimiento (MOU).
Las campañas de comunicación del CNCS han alcanzado más de dos millones de cuentas en redes sociales, logrando concienciar a la ciudadanía sobre prácticas seguras en entornos digitales. Estas iniciativas, orientadas a la cultura de la ciberseguridad, demuestran una comprensión avanzada del principio de “seguridad por diseño social”, donde la formación del usuario final es tan importante como la infraestructura técnica.
III. Capacitación y profesionalización del talento en ciberseguridad
Uno de los pilares del éxito del CNCS ha sido la creación de capacidades humanas. En colaboración con la Academia Cisco, el Instituto Tecnológico de Las Américas (ITLA) y Fortinet, el CNCS ha capacitado a más de 540 personas, incluyendo profesionales del sector público y privado (CNCS, 2024). Además, se han impartido 16 cursos técnicos especializados y 3 entrenamientos internacionales dirigidos a sectores críticos como el marítimo y el sanitario. Estas acciones posicionan al CNCS como un catalizador del talento cibernético en la región.
Los programas de concienciación ciudadana también han tenido un impacto significativo. Durante 2024, el CNCS desarrolló 12 campañas de sensibilización que alcanzaron a más de 2,000 participantes, con 800 personas inscritas formalmente en el programa nacional de capacitación ciudadana (CNCS, 2024). Esta estrategia evidencia una política pública que combina la seguridad técnica con la educación digital, alineándose con las mejores prácticas internacionales establecidas por la Unión Internacional de Telecomunicaciones (UIT, 2024).
IV. Comparación regional y posicionamiento
La comparación con otros países latinoamericanos permite ubicar objetivamente el desempeño dominicano. En 2024, el CSIRT Panamá reportó 1,312 incidentes, siendo el phishing y el fraude digital los más frecuentes (CSIRT Panamá, 2024). En contraste, el CNCS de la República Dominicana registró 1,600 casos en cinco años, lo que equivale a un promedio anual de unos 320 casos. Si bien Panamá presenta una mayor densidad de reportes, ello se explica por la amplitud de su red de monitoreo intersectorial.
En Colombia, el Centro Cibernético Policial registró 59,033 denuncias de delitos informáticos en 2023, y el sector privado estimó 12,000 millones de intentos de ataque ese mismo año (CCIT, 2023). Estos números, en gran medida resultado del tamaño poblacional y la economía digital de Colombia, superan los de la República Dominicana en términos absolutos, pero confirman que el volumen de 900 millones de intentos detectados por el CNCS es proporcional y consistente con su escala nacional.
En el Caribe, Trinidad y Tobago reportó apenas 205 ciberataques exitosos entre 2019 y 2024 (TT-CSIRT, 2024), mientras que Costa Rica, tras el ataque de ransomware de 2022, ha mantenido una estrategia de recuperación y resiliencia sin publicar datos comparables (OAS, 2023). A la luz de estas cifras, la República Dominicana se sitúa entre los países con capacidad técnica media-alta, destacando especialmente por su transparencia de datos y la implementación de plataformas de notificación y verificación, algo que no todos los países de la región han logrado.
El Índice Global de Ciberseguridad (GCI) de la UIT (2024) ubica a la República Dominicana en una categoría intermedia de madurez (“Tier 3”), junto a países como Panamá y Costa Rica, y por delante de varias naciones caribeñas menores. Este posicionamiento confirma que el país ha alcanzado un nivel de consolidación técnica y organizativa respetable, aunque con oportunidades de mejora en la integración de marcos normativos y la profesionalización avanzada del sector.
V. Estrategias y tácticas para fortalecer el servicio nacional de ciberseguridad
Para evolucionar hacia un servicio de ciberseguridad más robusto y efectivo, el CNCS podría adoptar una estrategia de tres ejes: integración normativa, fortalecimiento técnico y cooperación internacional ampliada.
Integración normativa y estandarización de métricas.
El CNCS podría alinear sus procedimientos de reporte con marcos internacionales como el National Institute of Standards and Technology Cybersecurity Framework (NIST-CSF) y los Incident Response Standards de FIRST. La creación de un modelo de reporte público anual, con series históricas estandarizadas, facilitaría la comparación regional y permitiría medir la efectividad de políticas sectoriales (NIST, 2022).
Fortalecimiento técnico y automatización.
El desarrollo de sistemas de inteligencia de amenazas (Threat Intelligence) basados en aprendizaje automático podría aumentar la capacidad predictiva del CSIRT-RD. Asimismo, expandir la cobertura de sensores de monitoreo a infraestructuras críticas —energía, salud, transporte y finanzas— reforzaría la detección temprana y la coordinación interinstitucional.
Cooperación y diplomacia cibernética.
Aumentar la colaboración con organismos multilaterales (OEA, UIT, BID) y con redes como CaribCERT permitiría compartir indicadores de compromiso en tiempo real y fortalecer la resiliencia regional ante amenazas transfronterizas. “Intelligence Liasion” con las agencias de inteligencia y contrainteligencia es, del mismo modo, imperativo. Un enfoque, centrado en la diplomacia cibernética, ampliaría la proyección internacional del CNCS y contribuiría al fortalecimiento colectivo del Caribe y “más allá”. Ciber-actores/ciberdelicuentes no conocen fronteras.
El Centro Nacional de Ciberseguridad de la República Dominicana ha demostrado un avance tangible en materia de gobernanza digital, gestión de incidentes, cooperación institucional y formación ciudadana. Los datos disponibles evidencian una estructura madura y en expansión, comparable con países latinoamericanos de mayor tamaño y con un liderazgo visible en el Caribe. Aunque persisten desafíos —como la estandarización de indicadores y la profundización de la cooperación técnica internacional—, los logros alcanzados entre 2020 y 2024 reflejan una política pública coherente y sostenible.
El CNCS, mediante la integración de marcos internacionales, el uso de inteligencia automatizada y la expansión de alianzas estratégicas, puede consolidarse como un referente regional de ciberseguridad. En un entorno global donde la seguridad digital se ha convertido en un pilar del desarrollo económico y la soberanía tecnológica, la República Dominicana está posicionada para ejercer un liderazgo ejemplar en el Caribe y América Latina.
Referencias
CCIT. (2023). Informe sobre ciberseguridad en Colombia 2023. Cámara Colombiana de Informática y Telecomunicaciones.
CNCS. (2024). Informe de resultados 2020-2024. Centro Nacional de Ciberseguridad, República Dominicana.
CSIRT Panamá. (2024). Reporte anual de incidentes 2024. Gobierno de Panamá.
NIST. (2022). Framework for Improving Critical Infrastructure Cybersecurity (Version 2.0). National Institute of Standards and Technology.
OAS. (2023). Cybersecurity Capacity Review: Costa Rica Post-Ransomware Assessment. Organización de los Estados Americanos.
TT-CSIRT. (2024). National Cybersecurity Report 2019-2024. Trinidad and Tobago Cyber Security Incident Response Team.
UIT. (2024). Global Cybersecurity Index 2024. Unión Internacional de Telecomunicaciones.